Do you feel like your current passwords are simply not up to the task of keeping your data safe and secure? If so, then it’s time to consider creating more secure, stronger passwords. In this post, we will look at how you can create better passwords that won’t be easily guessed or cracked by hackers.
Data is getting more valuable, so there’s no excuse for a lazy password these days. Need help? Rather than choosing an easy-to-remember piece of personal information, you can use more secure password management software instead.
We’ll discuss password managers and other techniques for making sure your accounts stay protected no matter what. So read on if you’re ready to increase your security and give yourself peace of mind!
Table of Contents
Do’s of Password Security
Do Make Your Passwords As Long As Possible
Hackers have multiple tools and techniques to get their hands on your private information. They can go the old-fashioned route and try randomly guessing at passwords, or they might use a “brute force” attack.
This uses computer programs that run through every possible letter/number combo faster than you can say “cybercriminal.” The effectiveness of this tactic varies wildly depending on how long and complex your password is – short ones stand virtually no chance, especially if the passwords are commonly used!
Consider Using Passphrases
Longer passwords are harder to break. The trick in coming up with longer passwords that don’t want to make you pull your hair out is to use passphrases. The best ones include random words and phrases that aren’t easily pasted from common sources.
Common sources include:
- Lyrics, verses, stanzas, and more from songs or poems.
- Quotes from speeches, conferences, or commencements.
- Quotes from movies, TV shows, or plays.
- Lines or passages from books and other publications.
If you want to use common sources, you can spice things up a bit by injecting:
- Grammatical errors (which this site is no doubt full of).
- Additional characters.
- Abbreviations.
- Memory devices like mnemonics.
- Phrases that are meaningful to you.
- Silly word replacements.
- Random words, also known as diceware. More on this is below.
- Iambic tetrameter, which is essentially your own poetry.
An iambus is a rhythmic unit in verse that consists of an unstressed syllable followed by a stressed one. And a tetrameter is a line of verse with four rhythmic units, more properly known as metrical feet. To learn more about this method, check out Do you find passwords too darn hard? Then poetry’s your hidden card! by Paul Ducklin from Sophos.
Diceware
Diceware allows you to string together random words to create a long passphrase. You use dice or a random number generator to compare your result to the specified word list. Stringing together 6 or more truly random words will allow you to create your next great passphrase.
Using a password manager? This technique works well for a master password! Then you can create long, complex, random passwords for each site using your password manager.
Check out the EFF Dice page for more information.
Do Make Your Passwords as Complex As Possible
Make your passwords as long and complex as you can. Use at least 16 characters, mixing letters, numbers, and special characters to create your next hard-to-guess password. Another popular method combines several random words (not words you like or prefer).
You can make this easier on yourself by using diceware or a password manager.
Do Use A Unique Password For Each Account
Do not reuse passwords. There are way too many breaches and counting to be reusing passwords across multiple sites, even if most of the sites you go to “don’t matter.”
When breached credentials are leaked, the leaked lists are circulated. Your information can be easily used multiple times to get into any of these other accounts. Use unique passwords (and usernames where possible) for everything.
Do Use A Password Manager
We are now at the point where you should be using a password manager. Password managers are services that safely store your user information and passwords and auto-generate strong passwords on your behalf.
The benefits are astounding and can free up your precious concentration. The benefits are:
- You don’t have to create your own passwords anymore (after the master password).
- Long, complex passwords can be automatically created based on your criteria.
- Password managers are designed to create and use passwords for each service easily.
- Plugins and extensions are available for your favorite browser.
- Strong encryption is used, along with syncing across multiple devices.
- Many password managers also offer password auditing and breach notification.
Just be sure to either create a strong master password or generate a random one using diceware. But don’t lose it! While you are at it, set up 2-factor authentication if you can.
Contested Password Security Advice
Changing Your Passwords Regularly
One of the oldest password maxims is that you should change your password often. Although it is great to change your password when it is necessary, most of the time, it’s not.
Guidance has changed in a version of NIST’s password guidelines (you can also look at NIST SP 800-63B, Section A.3), no longer advising the common practice of forcing password resets every few months. Instead of keeping attackers on their toes, people updated their passwords in predictable ways. They would add a date, the year, and the season or swap letters for predictable symbols like “1” for “I” and “$” for “s.”
Using Dictionary Words
There seem to be differences between defining a dictionary as a collection of common passwords versus an actual dictionary with all words.
Using a single dictionary word, especially a common word, is bad. However, using a combination of random dictionary words seems to be the right way to go about password security. This article from Crambler, for instance, argues that strength in passwords is length more than complexity.
One of the better methods of creating a long password is using diceware to generate 6 or more random words from a dictionary. Take this well-known example from xkcd 936 using 4 random words (considered secure at the time, use at least 6 now):
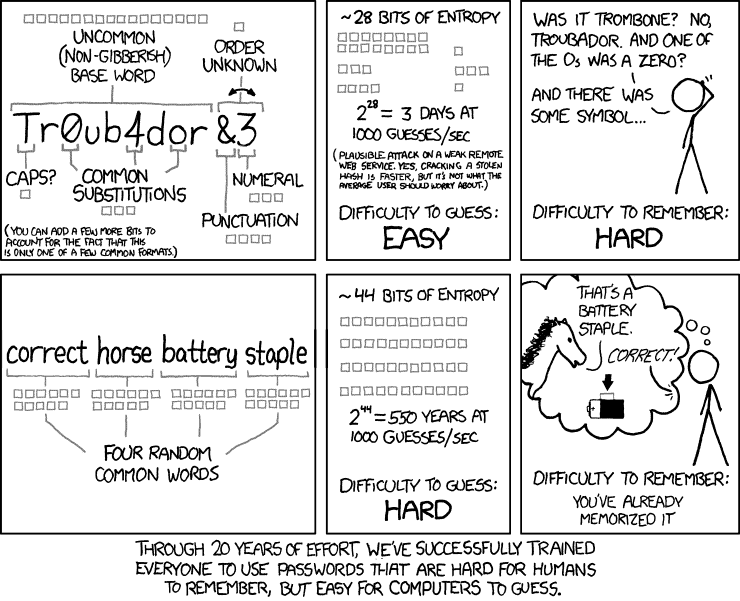
This advice created quite an uproar in the security community. People felt that this method would expose you to dictionary attacks, especially if the attacker has heard of this method and uses brute force combinations of 4 dictionary words.
This really isn’t the case, though. An attacker typically does not use an entire English dictionary to brute force this way. They typically use wordlists, and the chances of your truly random 6-word or more password would most likely not appear in any available list.
Password Security: Why the horse battery staple is not correct by Diogo Mónica, for instance, doesn’t agree with this method. From how he writes the article, it appears that he missed the point of the words being random instead of hand-picked. However, he does agree that you should just use a password manager and move on with your life. We are in agreement there. Password managers solve so many problems, so you really should be using them.
To jump more into this rabbit hole, check out this explainer from Explain xkcd to go over more of the controversies and responses.
Don’ts of Password Security
Don’t Use Examples of Good Passwords
If a support article displays an example of a good password, don’t use it! It’s mind-bending how lazy some people are. These example passwords are on multiple password lists by now.
Example from xkcd:
- “correcthorsebatterystaple”
Examples from Google:
- “Spooky Halloween” becomes “sPo0kyH@ll0w3En”
- “Later gator” becomes “L8rg@+0R”
Don’t Use Common Passwords With Trivial Modifications
Avoid using things like your name, friend’s name, pet’s name, birthday, significant dates, and more. Also, try to avoid using an easy to guess letter to symbol or letter to number substitution, such as changing “a” to “@” and so on.
And finally, refrain from using incremented passwords, such as “lighthouse1” to “lighthouse2.”
Don’t Use Keyboard Patterns
Do not use sequential characters on a keyboard, such as numbers in order or the widely used “qwerty.” As you look at common password lists, you’ll see increasing use of what is essentially someone rolling their face across the keyboard to form their password.
Besides “qwerty” and “12345,” there are more patterns known to hackers, which include:
- 1q2w3e4r
- 1qaz2wsx
- 1qazxsw2
- zaq12wsx
- !qaz2wsx
- 1qaz@wsx
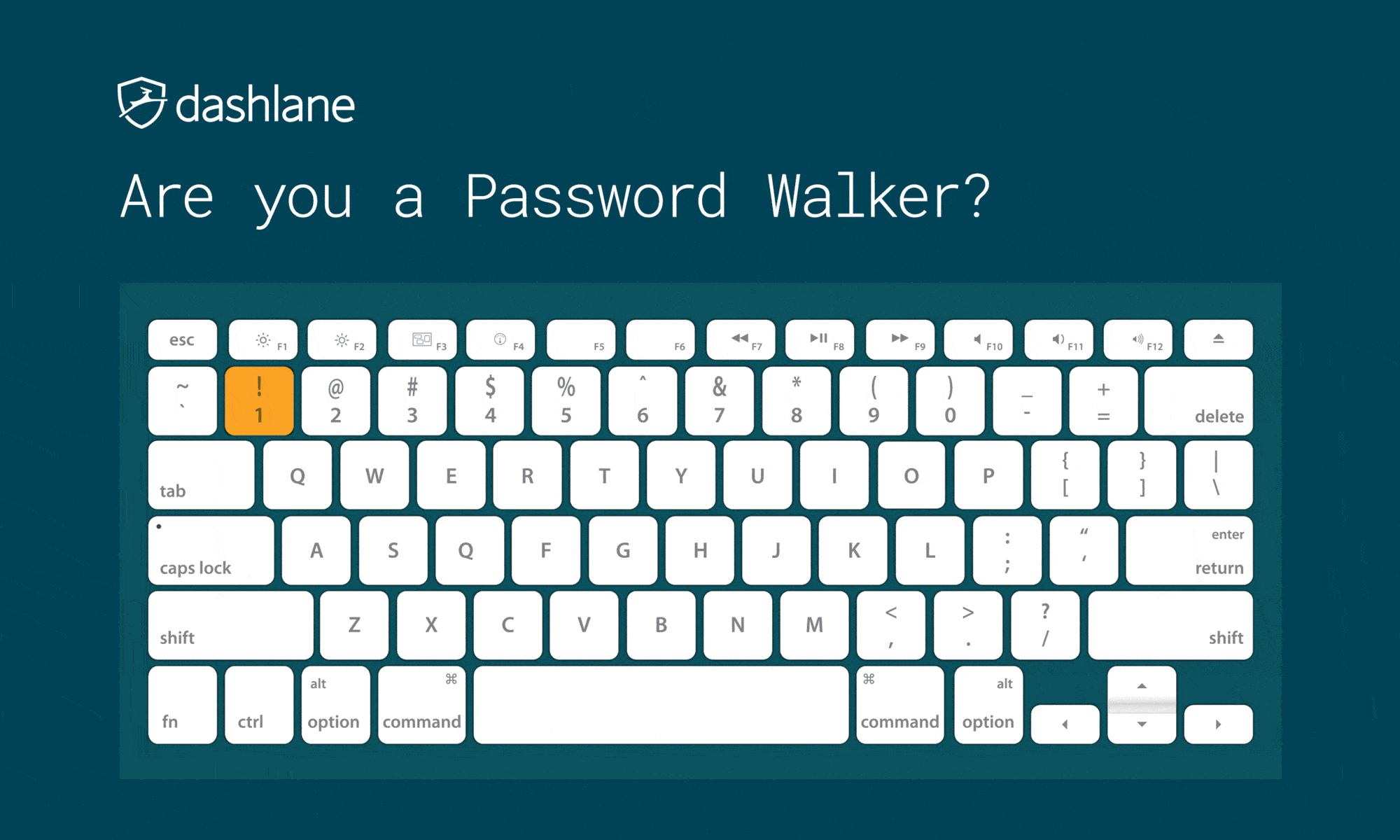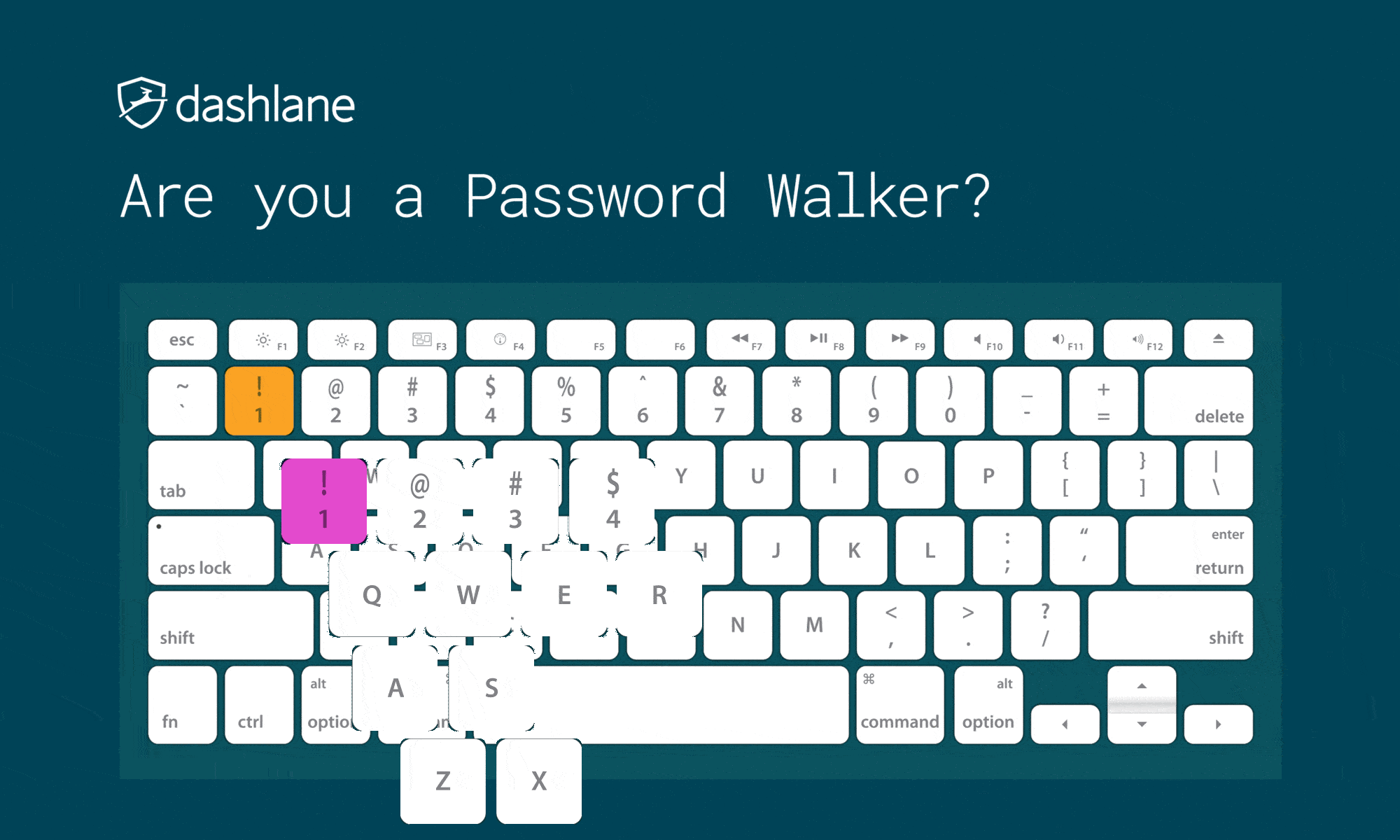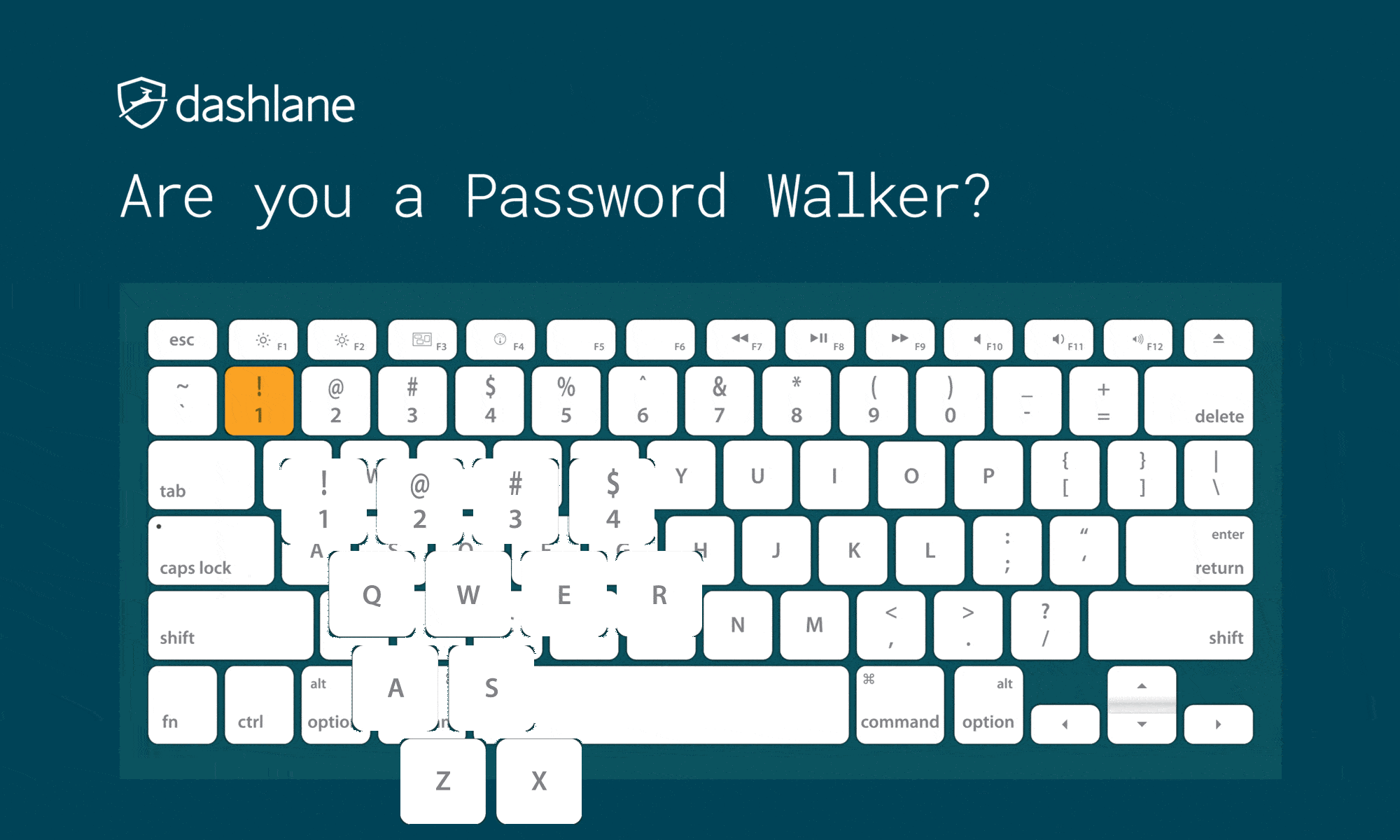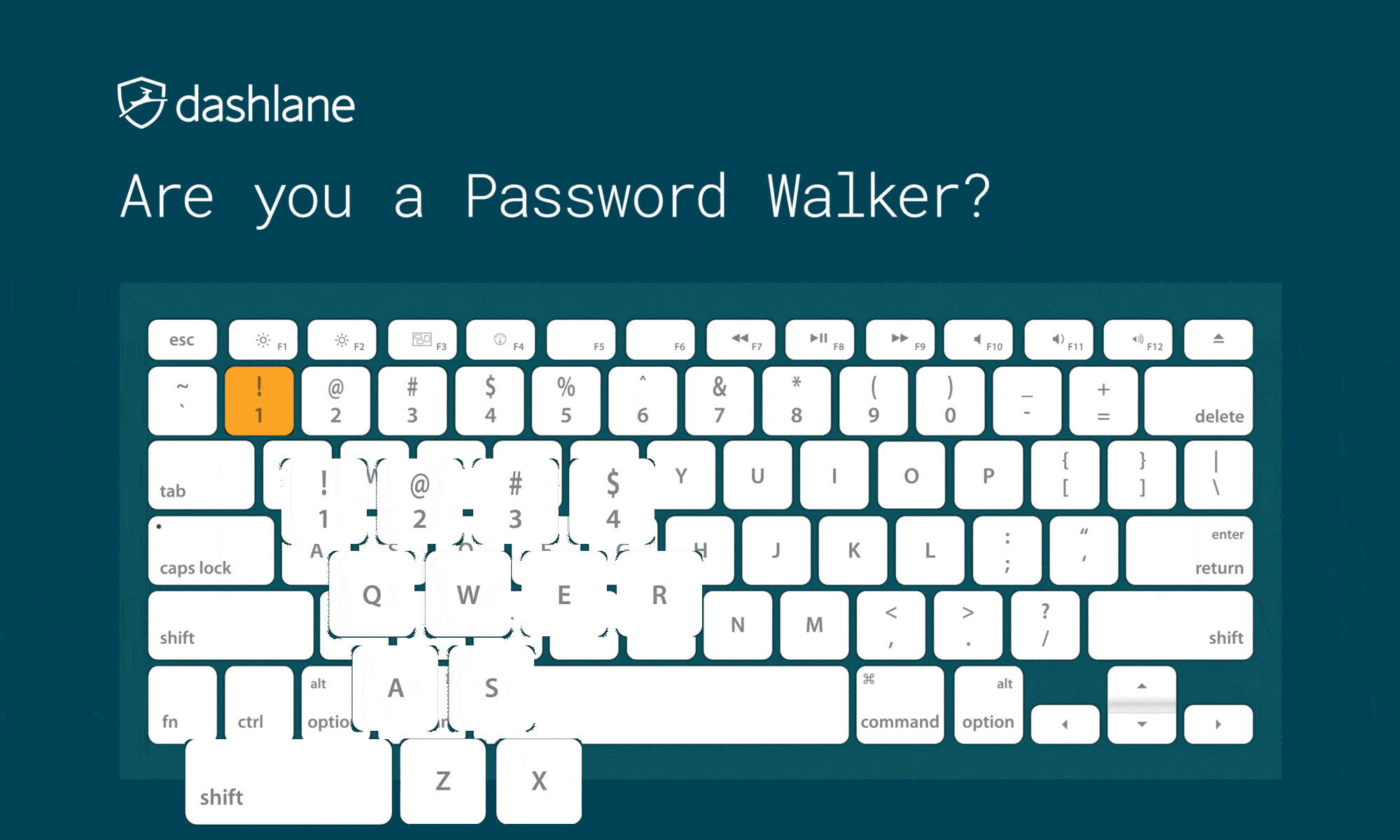
We have always called this method keyboard patterns, but we have seen this practice called “Password Walking” as well.
Don’t Use Personal Information
If information about you is easily discoverable, either through you or your network, do not include them in your password. These make your password easier to guess.
Easily discoverable information about you includes:
- Pet names
- A notable date, such as a wedding anniversary
- A family member’s birthday
- Your child’s name
- Another family member’s name
- Your birthplace
- A favorite holiday
- Sports Teams
- Birthdays
- Pet’s Names
- Season / Month / Year
- Address
- Regional Interests
- Something related to your favorite sports team
- The name of a significant other
- The word “password”
Similarly, if you must choose security questions and answers when creating an online account, select ones that are not obvious to someone browsing your social media accounts.
Don’t Share Your Passwords
Don’t give out your passwords to anyone else. If a service offers delegation or some type of sharing option, do that instead. Furthermore, don’t save your password in a browser on a shared computer.
It’s also best not to type your password directly in front of someone or keep a handwritten note with your password on it in an unsecured location. If you need to write your password down in a journal or sticky note, keep it locked up when not in use.
What To Do When You Find a Password To Update
You can easily avoid problems by maintaining good password hygiene for future passwords, but what about previously badly constructed passwords? Well, here’s what you do about it:
- You can use Have I Been Pwned to check if your email was ever in a breach. Just because a site doesn’t appear here doesn’t mean it hasn’t been breached. You may never find out about breaches on smaller websites.
- Go over all the accounts you have and delete the accounts you no longer use from the website first.
- Check dormant accounts for suspicious logins and other activity. If you notice something strange, be sure to change your password immediately while you still can. Also, terminate strange login sessions if possible.
- Update all of your shorter and non-complex passwords to unique, complex ones. Use the password generator feature in your favorite password manager to make this a piece of cake.
- Use 2FA where you can, when you can. Use an authenticator, token generator, or hardware key where possible in lieu of SMS texts. SMS codes are better than nothing, though.
Final Thoughts
Whether you’re a tech whiz or someone who uses their computer occasionally, learning how to create stronger and more secure passwords can make all the difference in protecting yourself and keeping your data safe.
There’s no guarantee that these techniques will prevent an attacker from learning your password, but they will make it much more difficult. We hope you learned some valuable tips and tricks to create better passwords to use them confidently. Be safe!

